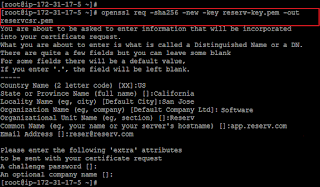
link referensi dari sini
download disni : https://drive.google.com/open?id=0B8GDi0lY8FDgQ0RCZVFFdVg4d3M
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk65210
download disni : https://drive.google.com/open?id=0B8GDi0lY8FDgQ0RCZVFFdVg4d3M
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk65210
SSL Network Extender E75
| Solution ID | sk65210 |
| Product | SSL Network Extender |
| Version | E75 |
| Platform / Model | Intel/PC |
| Date Created | 09-Oct-2013 |
| Last Modified | 10-Feb-2016 |
Solution
Table of Contents
Note: SSL Network Extender requires that Java is installed on the endpoint computer. Java is not installed on Mac OS X 10.7 (Lion). For more information see sk65144 (SSL Network Extender - Java Availablity).
Important: R70.40 Security Gateways must have the security hotfix installed as described in sk62410. Failure to do so can make the Security Gateway susceptible to attacks.
Windows
Macintosh
Note: All Linux OSs require Oracle JRE to install.
Use the snx -h command to make sure that the SSL Network Extender client is installed correctly.
Note: In order to download some of the packages you will need to have a Software Subscription or Active Support plan.
SSL Network Extender E75 for Security Gateway R70.40
SSL Network Extender E75 for Security Gateway R75.20
Related Links:
-
Overview
-
What's New
-
Supported Security Gateways
-
Endpoint Platforms
-
Linux Supported Platforms
-
E75 Documentation
-
E75 Downloads
| For more information on Check Point releases see: release map, upgrade map, backward compatibility map. | |
| For more information on SSL Network Extender E75, refer to sk65669 (SSL Network Extender E75 Known Limitations).You can also visit our Mobile Access / SSL VPN forum or any other Check Point discussion forum to ask questions and get answers from technical peers and Support experts. | |
| See sk91060: Removing old Check Point packages and files after an upgrade. |
Overview
SSL Network Extender is a secure connectivity framework for remote access to a corporate network. SSL Network Extender uses a thin VPN client installed on the user's remote computer that connects to an SSL-enabled web server. The web server and the client are in the same VPN.Note: SSL Network Extender requires that Java is installed on the endpoint computer. Java is not installed on Mac OS X 10.7 (Lion). For more information see sk65144 (SSL Network Extender - Java Availablity).
What's New
These features are new for SSL Network Extender E75:- Support for Mac OS X 64-bit.
- Support for new Linux platforms 32 and 64-bit.
- Proxy server auto-detection is now supported for browsers that run Java or ActiveX.
- Improved user experience that explains how to install Java when necessary.
Supported Security Gateways
This hotfix can be installed on top of these Security Gateways (refer to "E75 Downloads" section below):- R70.40
- R71.40
- R75.10
- R75.20
- VSX NGX R67.10
Important: R70.40 Security Gateways must have the security hotfix installed as described in sk62410. Failure to do so can make the Security Gateway susceptible to attacks.
Endpoint Platforms
SSL Network Extender is supported on these Operating Systems.Windows
- XP Home and Professional (SP2, SP3) (32-bit and 64-bit)
- Vista (SP1) (32-bit and 64-bit)
- Windows 7 (including SP1) Ultimate, Enterprise, Professional, and Home (32-bit and 64-bit)
- Windows 8 (all versions and editions, not including Windows RT)
Macintosh
- Mac OS X 10.6.8 (Snow Leopard) (32-bit and 64-bit)
- Mac OS X 10.7, 10.7.1, 10.7.2, 10.7.3, 10.7.4, 10.7.5 (Lion) (32-bit and 64-bit)
- OS X 10.8, 10.8.1, 10.8.2 (Mountain Lion) (64-bit)
- OS X 10.9.x (Mavericks)
- OS X 10.10 (Yosemite)
- Ubuntu 11.10 (32-bit and 64-bit)
- openSUSE 11.4 (32-bit and 64-bit)
- Fedora 15 and 16 (32-bit and 64-bit) (Requires xterm (standard terminal emulator) for deployment)
- RHEL 5.7 and 6.1 (32-bit and 64-bit)
Note: All Linux OSs require Oracle JRE to install.
Use the snx -h command to make sure that the SSL Network Extender client is installed correctly.
Linux Supported Platforms
| Latest Linux Distribution | 32-bit Prerequisites | 64-bit Prerequisites |
| Ubuntu 11.10 | libstdc++5 (i386) | libstdc++5 (amd64) |
| Ubuntu 12.04/12.10 | libstdc++5 (i386) |
|
| Ubuntu 14.04 | libpam0g:i386
libx11-6:i386 libstdc++6:i386 libstdc++5:i386 |
libpam0g:i386 libx11-6:i386 libstdc++6:i386 libstdc++5:i386 |
| openSUSE 11.4 | libstdc++33 |
|
| openSuSE 12.2 | compat-libstdc++ |
|
| Fedora 15 |
|
|
| Fedora 16/18 |
|
|
| RHEL 5.7 | None | None |
| RHEL 6.1 | Same as Fedora 16 32-bit | Same as Fedora 16 64-bit |
E75 Documentation
Important: You must read the instructions in the Release Notes before installing the relevant download.- SSL Network Extender E75 Release Notes
- sk65669 - SSL Network Extender E75 Known Limitations
- sk67141 - SSL Network Extender not launching using 64 bit web browser in Windows
- sk90240 - SSL Network Extender E75 CLI Support for Mobile Access Blade
E75 Downloads
Important: Installing SSL Network Extender consists of two parts:- Upgrading SSL Network Extender on Security Gateways
- Deploying the clients from the Security Gateways to endpoint devices
Note: In order to download some of the packages you will need to have a Software Subscription or Active Support plan.
SSL Network Extender E75 for Security Gateway R70.40
- SSL Network Extender E75 for Security Gateway R70.40 Hotfix - SecurePlatform
- SSL Network Extender E75 for Security Gateway R70.40 Hotfix - Solaris
- SSL Network Extender E75 for Security Gateway R70.40 Hotfix - IPSO
- SSL Network Extender E75 for Security Gateway R70.40 Hotfix - Windows
- SSL Network Extender E75 for Security Gateway R71.40 Hotfix - SecurePlatform
- SSL Network Extender E75 for Security Gateway R71.40 Hotfix - Solaris
- SSL Network Extender E75 for Security Gateway R71.40 Hotfix - IPSO
- SSL Network Extender E75 for Security Gateway R71.40 Hotfix - Windows
SSL Network Extender E75 for Security Gateway R75.20
- SSL Network Extender E75 for Security Gateway R75.20 Hotfix - SecurePlatform
- SSL Network Extender E75 for Security Gateway R75.20 Hotfix - Solaris
- SSL Network Extender E75 for Security Gateway R75.20 Hotfix - IPSO
- SSL Network Extender E75 for Security Gateway R75.20 Hotfix - Windows
Related Links:
| This solution is about products that are no longer supported and it will not be updated |